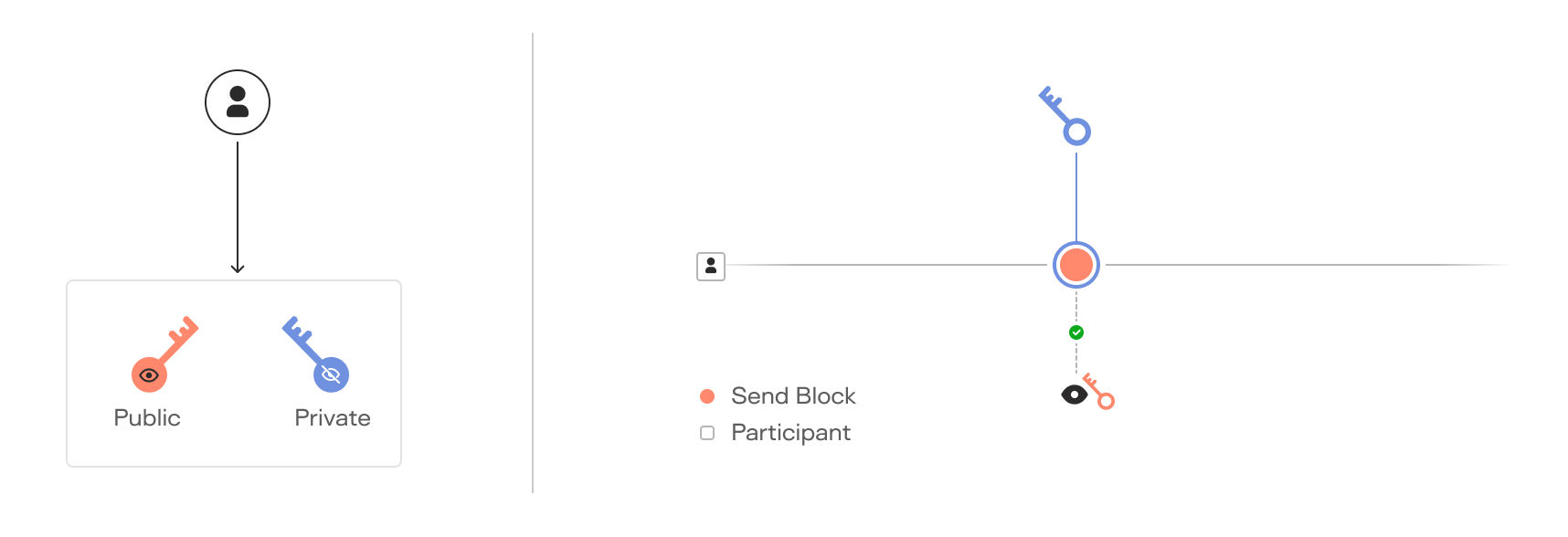
Key Pairs
In the world of digital transactions, a key pair is like your personal lock and key set. It consists of a public key that can be freely shared, and a private key that is kept secret. On the Keeta Network, when a user makes a transaction, they use their private key to 'sign' it, creating a unique stamp. Anyone can then use your public key to verify that you indeed created the unique stamp, similar to how a bank verifies your signature on a check, but far more secure and impossible to forge.
The Keeta network allows participants to manage their own key pairs, offering flexibility and security. The user has direct control over their transactions – no party can act on their behalf without their private key. Even if someone obtains your public key, they can't use it to make transactions or access your assets; only the private key can do that.
This key pair system brings several advantages to Keeta. It ensures transactions are secure and tamper-proof, providing an accurate record of what party made each transaction – crucial for financial operations. Whether an individual makes a single payment or a crypto exchange manages millions, Keeta's key pair system provides the security and flexibility needed.